
Security | Encryption | Complicance
Infrastructure Security
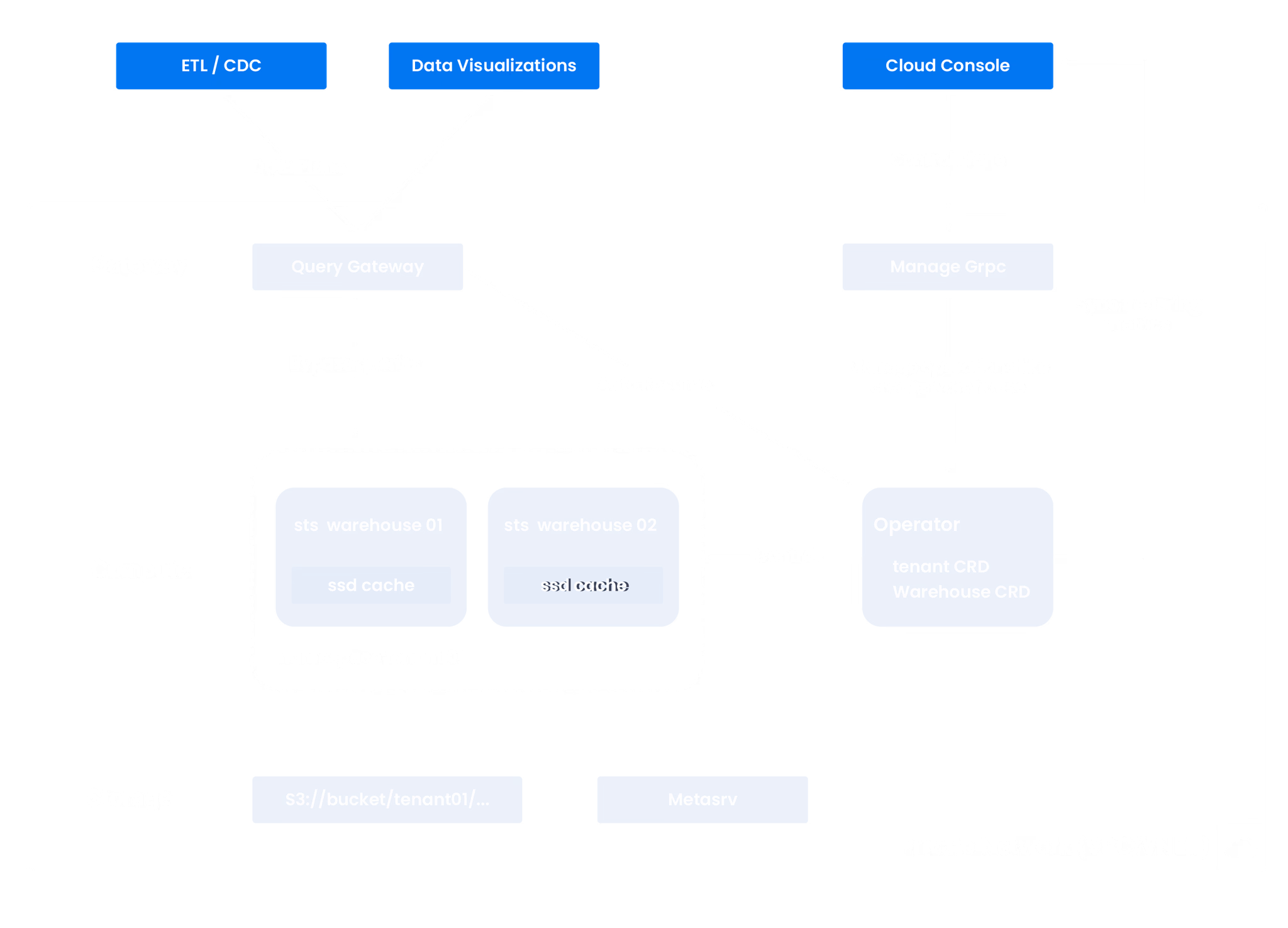
Physical infrastructure
Databend Cloud is currently deployed on GCP and AWS hosted Kubernetes clusters with all servers located across the globe, including the United States. We use isolated, stateless pods to visit internal storage with ephemeral caches.
Data Security and Encryption
Data Access Permission Control
We have strict data access isolation among tenants. There is no long-term access key stored on Databend cloud. In order to minimize data leakage risks, we rotate our data access key regularly with least-privilege permission requirements.
We use data-encryption and identity authentication services provided by cloud providers. It can provide a service with an automatically rotated Token (for example, automatically expires in half an hour), and establish an identity association with the IAM Role through the STS service of the cloud vendor, and then restrict the access rights of the service through IAM rules to achieve fine-grained access control.
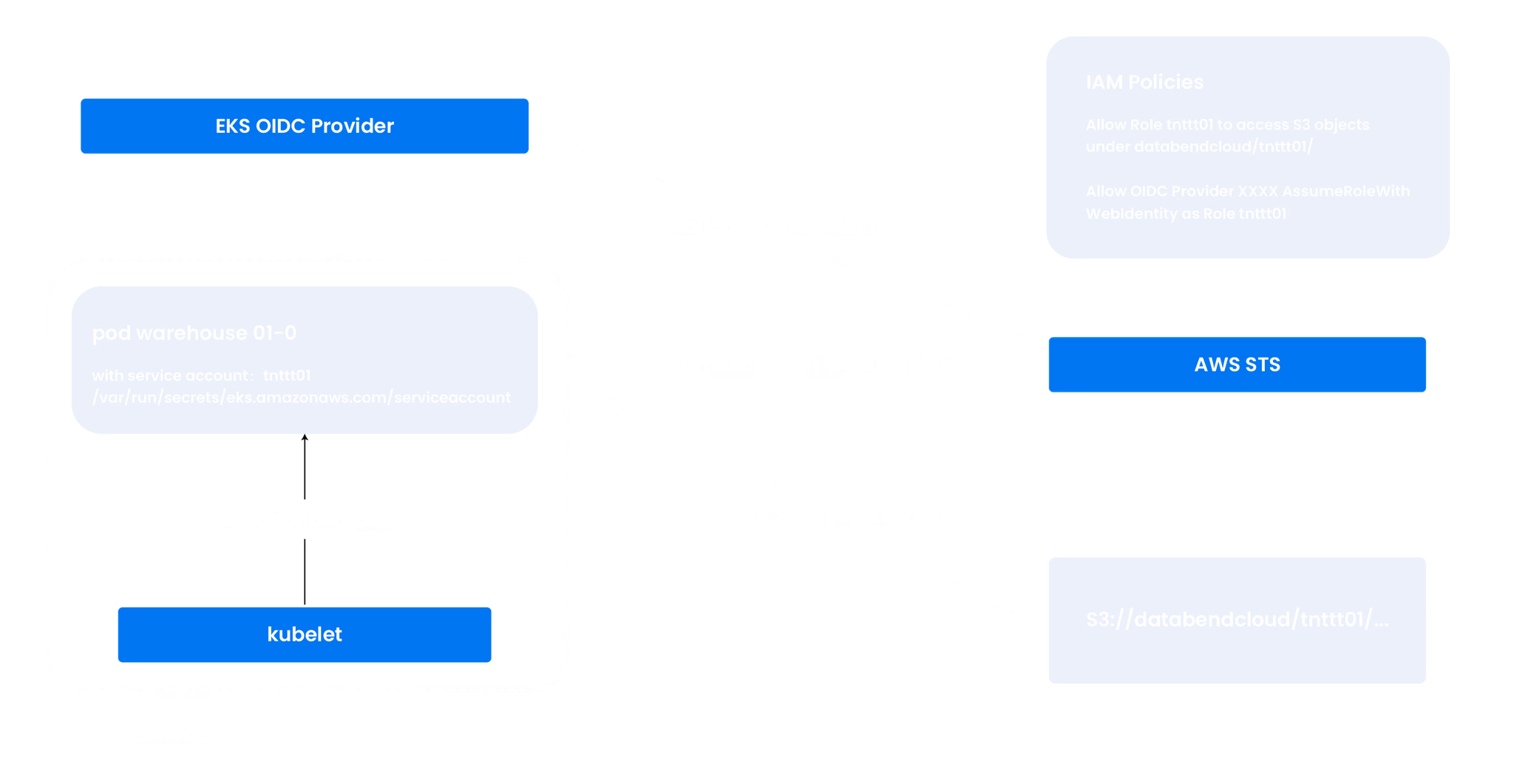
In Databend Cloud, each tenant is assigned a dedicated IAM Role and a dedicated encrypted bucket for data storage.
The IAM policies are configured to restrict each tenant's access to specific storage locations. This eliminates the need for long-lived access keys, making access to cloud resources such as S3 more secure and reliable.
Data Encryption In The Rest
All data stored on Databend Cloud is encrypted by default using server side encryption with dedicated KMS. Additionally, users can also leverage the Assume Role mechanism in Databend Cloud to mount their own S3 buckets from their AWS accounts for analysis purposes. Databend only supports decrypting and encrypting data in memory on dedicated warehouses.
Network Security
Securing Communication In Transit
We provide end-to-end encryption for all communication. All customer data-flow are solely over HTTPS. Connections encrypted using TLS 1.2 from clients through to the Databend API gateway.
Restricting Network Access through VPC private link
PrivateLink provides enhanced network security by connecting to Databend cloud cluster over VPC peering. Customers can initiate the connection to the desired service using a VPC endpoint, which can be further configured with security groups to create trust boundaries and control access to the endpoint. Currently, this feature is only available on AWS. If your team has special concern about other cloud providers, please reach out to our support team.
Network Policy Enforcement
Databend supports users to configure network IP allow lists and blocked lists in network policy.
It allows you to define sets of rules governing the allowed and blocked IP address ranges for specific users, effectively controlling their network-level access.
Data Access Control
RBAC & DAC access control
Databend offers a range of privileges that allow you to exercise fine-grained control over your database objects.
Customers control RBAC completely, meanwhile, DAC (Discretionary Access Control) also applies to the role customer created that owns the object.
For details on the privileges for each database object, please take a look at our document.
Column-based access control
Databend allows users to config column-wise data visibility by creating data masking policies. Data masking policy would transform data and rewrite or hide given columns based on the current analyzer's role dynamically.
Government and Industry Security Compliance Efforts
Databend currently collaborates with Vanta to meet compliance standards including SOC-2 Type-2 and GDPR.
Our compliance efforts for Databend Cloud include:
- SOC 2 Type II assessment: An independent third-party has thoroughly conducted a SOC 2 Type II assessment, affirming the robustness and effectiveness of our operational controls. Emphasizing our commitment to security and excellence, we continuously monitor and enhance our operational controls and defenses against vulnerabilities. Our dedicated team ensures these standards are upheld without compromise. We are scheduled to receive the next audit report by August 2024
- GDPR compliance: Our GDPR compliance hinges on strict data privacy enforcement, robust encryption, and regular privacy audits to shield personal data from unauthorized access. We enforce stringent access controls, permitting only a select group of trained security personnel to access and monitor our infrastructure and operational logs, ensuring the highest levels of data protection and compliance.
Subscribe to our newsletter
Stay informed on feature releases, product roadmap, support, and cloud offerings!



